You are a human firewall.
As IT professionals we can put up spam filters, antivirus software, firewalls and advanced email filtering techniques in your IT environment to limit the number of malicious emails that get to you – but we can’t filter out every attempt.
At some point you’ll be the last line of defense for the business you work for.
WHAT IS PHISHING?
Phishing is a common type of online scam where criminals try to steal sensitive information from individuals and the businesses they work for. These criminals try to lure victims by impersonating legitimate organizations through emails, text messages or advertisements.
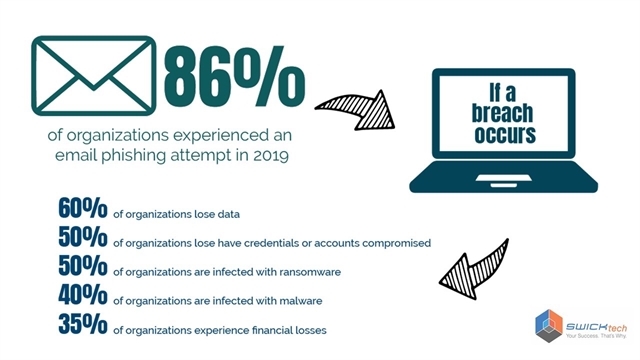
Phishing scams can be quite common. According to reports, in 2019 86% of organizations in the United States experienced an email phishing attempt. Of those compromised, 50% were compromised with ransomware and 35% experienced financial loss.
FIVE TIPS TO AVOID BEING COMPROMISED BY A PHISHING ATTACK
- Watch out for poor spelling or grammar
While scammers could be targeting you from anywhere on the globe, oftentimes phishing attempts come from overseas in countries like Russia, Nigeria, China or North Korea where laws against cybercrimes are non-existent or not enforced.
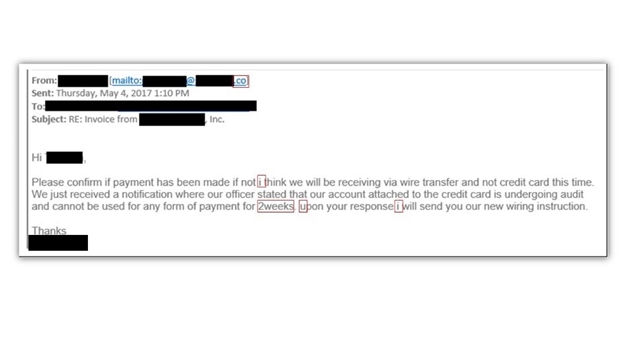
The example above shows poor spelling in an email phishing attempt.
- Be wary of requests for sensitive information
Compromises happen when a phishing attempt collects information from a victim. Whether you reply to an email with sensitive information or you accidentally give up credentials, the criminals have succeeded. - Attachments can carry malicious intent
A downloaded attachment from an illegitimate email could contain malware, leading to a serious compromise for the business you work for. Most sophisticated compromises can happen if you download a file that looks to be real and legitimate.
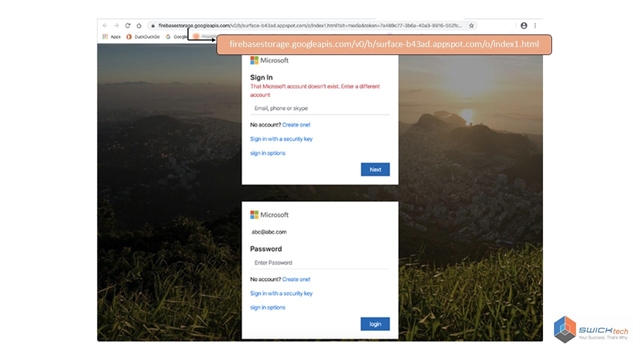
The above example shows a common type of phishing attempt. It begins with a fake email asking a victim to open, what looks to be a known file type, requiring a username and password. The file points to a fake webpage for access and collects credentials for the criminals.
- Know the Email Sender
An illegitimate email can hit your inbox and look like it’s coming from a trusted organization or someone you know. One way to stop a phishing email in its tracks is to know the sender of the message. Attackers tend to use domains that sound legitimate. In reality they have no association with the company they’re attempting to represent. Look for the domain after the “@” symbol and before the “.com, .net, .org (etc)”.
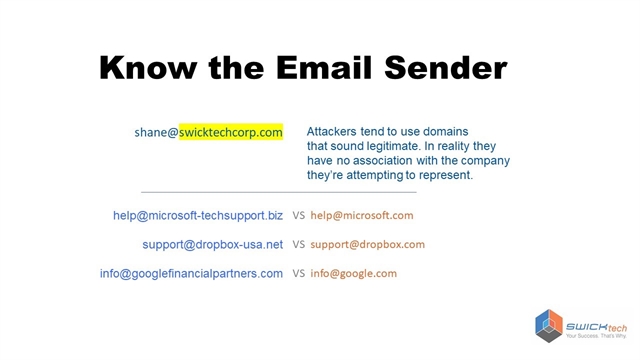
In the above example, shane@swicktechcorp.com is fake domain. SWICKtech’s email domain is SWICKtech.com – so the legitimate email from Shane would be Shane@SWICKtech.com. Here are a couple other examples of fake domains next to real ones.
- Hover over your links
Links in an email are a red flag for malicious activity. If you hover your mouse over a link in an email – it will show you the URL that the link points to.
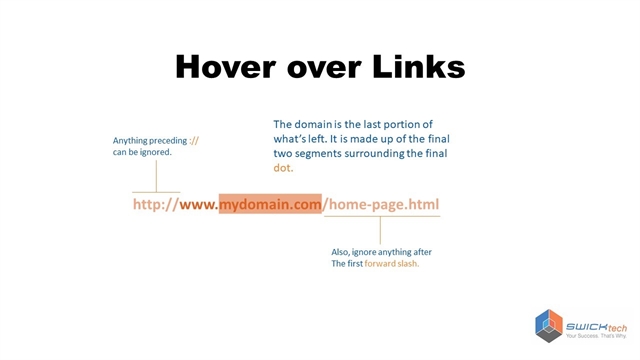
Make sure the domain portion of the webpage is legitimate. In this example above the domain is the orange part of the URL – after the “www.” and before the first “/”
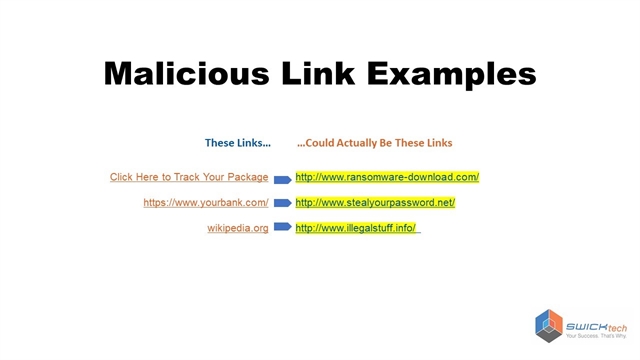
Be wary of links that are renamed – as you can see in the above example, a seemingly innocuous link can be quite damaging if it is followed to a malicious page.
HERE’S WHAT YOU CAN DO
The ability to detect and avoid malicious phishing emails is extremely valuable for any business. Sometimes businesses run phishing tests to find out who on staff is vulnerable or needs cybersecurity awareness training.
If you spot a phishing scam in your inbox, the best thing to do is report it to SWICKtech – if you’re a SWICKtech client – or to your IT staff.
If you’re interested in learning more about implementing cybersecurity tools to your business IT environment, we’d be happy to have a no-strings-attached conversation about our services at SWICKtech.