
How much is your company’s data worth to you? What is the cost to your business if either of the following occurred?
I once evaluated a new client’s existing network infrastructure. She wanted to know why we were suggesting that she spend money on the Firewall and Wireless Access Points we recommended, when her current solution was working “just fine.”
I pulled out my cell phone, a beat-up old Droid2. I connected to the wireless network they had configured. For the convenience of their visitors, they had the wireless ID and password for their “guest” wireless printed on a card at the reception desk.
I then launched a free app that I’ve used countless times for network troubleshooting, and two thumb-taps later I was scanning what should have been a separate guest network that connects only to the Internet. Instead, I was seeing information about every machine on their internal network. The workstations, laptops, cell phones and tablets, the servers and the router were all mine to view and probe at my leisure.
- Suddenly, you can’t access your financial statements, credit card transactions, accounting data, archived emails, customer database, client correspondence, or website. Or…
- Suddenly, your biggest competitor, or an identity-theft ring, can access all of it.
- Suddenly, you can’t access your financial statements, credit card transactions, accounting data, archived emails, customer database, client correspondence, or website. Or…
- Suddenly, your biggest competitor, or an identity-theft ring, can access all of it.
With the right network security solutions in place, the above scenarios become vastly more difficult for an intruder to accomplish.
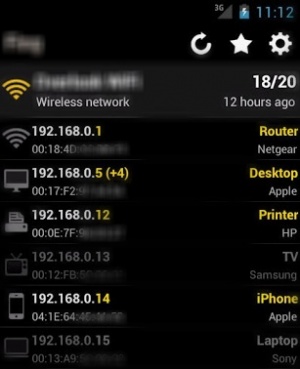
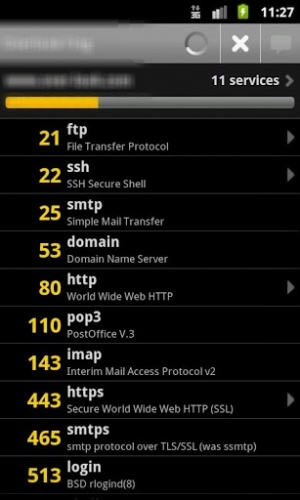
I tapped my thumb on their main server, and scanned for open ports. I was able to tell my client things about her server’s roles and configuration, having neither seen it nor logged into it.
My free network-scanning software told me the manufacturer of their consumer-grade router, and a quick Google search revealed the default login credentials.
Username: admin Password: password
Another thumb-tap on my phone opened the configuration page of their router in a web browser. I logged in. The default credentials hadn’t been changed. The person who installed it had just plugged it in and used the default settings – and that was good enough for them.
There is a long list of things I could have done from this point forward, if I had a selfish or malicious intent. Here are just a few:
- Reconfigure the router to break the internal network and lock them out by changing the password to something only I know, or;
- Set up remote access to their internal network, so I could probe their computers later from the comfort of my home, or;
- Use their Internet feed to send spam emails, propagate viruses, or “share†pirated software.
Two common mistakes put me in the driver’s seat over their entire infrastructure, and I didn’t even have to break in, I just walked through open doors. Physical proximity is not required for this. A wireless network can be hacked from miles away with a simple antenna.
With the right hardware, properly configured – and a bit of thought about network security when planning the network – I wouldn’t be in this position.
How secure is your network?



