A CLEAR-CUT GUIDE TO FIREWALL SECURITY
Communication is the gateway to success, yet so many information technology professionals are faced with challenges when explaining terminology, concepts and procedures to their non-IT colleagues. Much of the time, this is because the IT industry can change fairly quickly—and sometimes it’s hard to keep up.
But when it comes to network security, it’s important to understand some basic concepts so you can keep your systems locked down and your business protected. One of the big ones? Understanding firewall security. Here’s your guide to understanding firewall security—in plain English.
Dangers Lurking Beyond Your Firewall: Data Theft & Identity Theft
Simply put, you need a strong firewall. Viruses, spyware, phishing emails, Trojan horses, worms, malware, bot armies, ransomware, scareware, hackers and cybercriminals…yeah, there’s all kinds of dangers lurking out there. You’ll hear these top network security terms used nearly interchangeably—and while they’re not all the same, the reason for this is because every one of these threats attempts to do essentially the same thing: steal sensitive data for criminal activity. Whether they invade to gain access to your clients’ personal data files, steal credit card and/or bank account information, or manipulate a system to funnel data to some other location, data and identity theft are far too common threats.
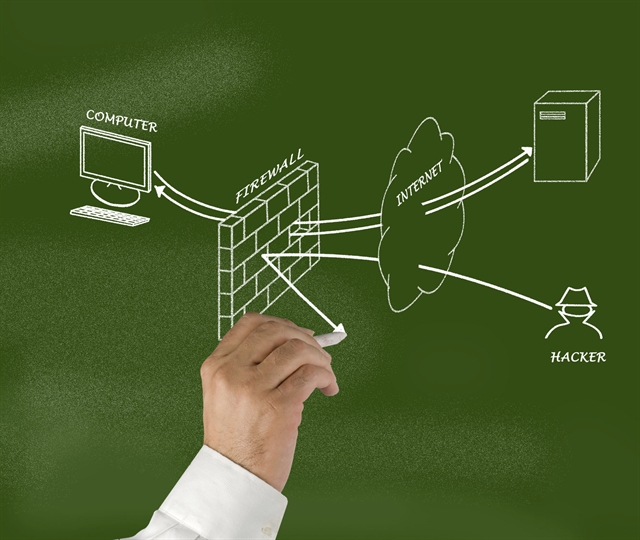
So What’s a Firewall?
A firewall is the barrier between a company’s private, internal network and the rest of the Internet. Picture it as a literal wall constructed between your computer and the outside world. Just as a real-world, tangible firewall protects property against destructive forces and the spread of those destructive forces, same goes for your network firewall, but it protects your company data, your computer assets, and the wellbeing of your business.
Acting as a gatekeeper, the firewall is crucial for evaluating and protecting ALL ingoing and outgoing data—from email to live streaming video conferences to website access, nothing gets in or out of a system without passing through the firewall first. Because of the vital role your firewall plays in your network security, its management is paramount to system-wide security. Your firewall must be monitored, adjusted and fine-tuned on a regular basis. Access permissions require regular attention and preventative maintenance is a must to ensure your firewall is updated and functioning in tip-top shape.
Your Firewall in Action
Put simply, your IT team uses a program or a piece of hardware to define certain rules for how your employees access a variety of things on the Internet. Allow and Deny permissions are assigned to ensure only approved computers and employees have access to particular websites, documents, programs, and other information found on the Internet. Without a secure firewall in place, if one employee accidentally downloads a malicious program, your entire network could be compromised and destroyed. With a solid firewall in place, that employee’s permissions don’t allow them to access that malicious program in the first place, minimizing network security risks.
Firewall Best Practices
The next step to understanding firewall security is to understand these essential IT industry best practices. At minimum, your IT team should follow these guidelines when developing and implementing a secure firewall.
—>Clearly define all firewall policies
—>Clearly define and create a system for documenting any changes to firewall policies and procedures
—>Clearly define and control who is in charge of your firewall and who has permission to enact any policy, procedural or structural changes to the firewall itself
—>Schedule regular testing of the effectiveness of your firewall
—>Schedule regular firewall security audits
—>Proactively monitor and control firewall access points to catch suspicious activity early
—>Ensure procedures are in place to regularly update firewall software
—>Ensure you have a disaster recovery plan and regularly scheduled backups in place at all times to ensure your company can recover if your firewall is breached
Decoding Firewall Security
Using this information as a guide, you’ll be able to better communicate with your IT professionals to ensure your firewall is stable and secure. Just remember to ask questions; nobody expects you to become an expert in this field if you’re not an IT professional yourself. Better safe and secure than sorry!