MANAGED IT SERVICES AND EXPERT SUPPORT FOR YOUR BUSINESS
Serving our Clients for Nearly 20 Years
Bytes of Data Lost
Years of Experience
Clients Served
Endpoints Protected

Cybersecurity
Our cybersecurity plans for businesses in Wisconsin and surrounding areas include SOC (Security Operations Center) services and come with certified cybersecurity agreements to make your business ultra-secure and compliant. Our cybersecurity solutions also include cybersecurity insurance compliant plans for CMMC 2.0 (Cybersecurity Maturity Model Certification).
Managed IT Services
From providing business IT (Information Technology) infrastructure management to automating advanced security, SWICKtech’s managed services plans (MSP and MSSP – Managed Security Services Provider) serve companies in Illinois and nearby regions with unlimited help desk support to help them become efficient and productive.


Compliance
Our team of Wisconsin Government IT Compliance consultants will build you an environment where compliance standards and regulations are met and exceeded.
Get To Know Us
SWICK Technologies is an IT Managed Service Provider (MSP) that has been serving Southeastern Wisconsin and Northern Illinois for 18 years. We believe that companies can unlock growth by embracing technology to better serve customers and employees. True believers in the “client first” approach, we craft success by working closely with our clients to build exactly what they need.
Our company growth and culture are achieved through dedication to our core values:
Ensure Client Success

Develop Relationships

Be Open and Honest

Have Fun Every Day
Be Passionate about whatever you do
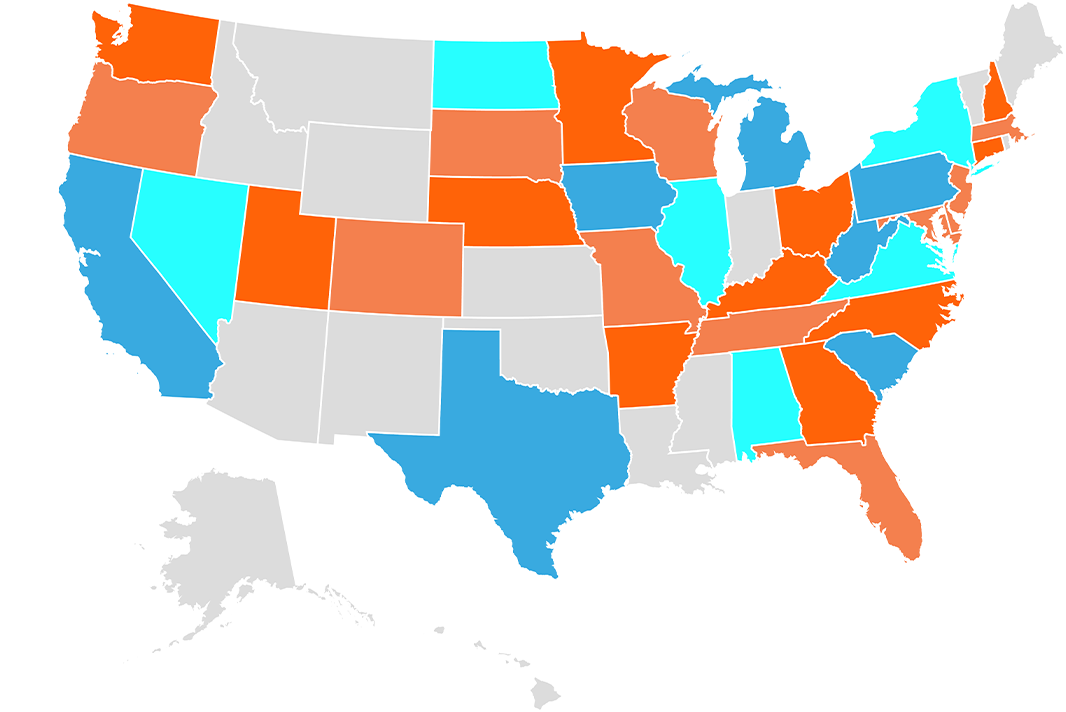
Supporting Clients Globally
Trusted Partners
SWICKtech is a certified Microsoft, Fortinet and Cisco Partner and an authorized Dell and HP dealer (among others) with extensive experience in the small- and medium-sized business space.
SWICKtech is also a Tier 1 Cloud Service Provider (CSP) for all M365 and Azure licensing needs. Contact us today to learn how you can get top tiered engineering support directly through our CSP connections!






Swicktech Blog

Payroll Diversion Fraud Is Targeting Employees

SWICKtech’s New Cybersecurity Agreement Makes Implementing New Cyber Insurance Requirements Easy

What Is the Log4J Vulnerability?
Testimonials
How can we help you?
We’re happy to offer a free, no-strings-attached consultation about any IT or technology issue that you’re having at your organization.
"*" indicates required fields
Join Our Team
SWICKtech offers a collaborative environment in which employees are consistently learning while solving a variety of challenges for our clients.
Our passion for IT and evolving technologies is the driving force behind our mission to develop professional, lasting relationships with our clients and ensure their success in our business.

